Human Zombification as an Information Security Threat

China and Russia share an information security doctrine, one that is significantly different from Euro-Atlantic doctrines. In the Chino-Russian model of information space a discussion about population zombification does happen and it fits squarely within the domain of information security. No, this is not an Onion article.
China and Russia have significantly broader definitions of Information Security than US, UK and other mostly aligned Euro-Atlantic nations. Fundamentally different conceptual approaches to information security are behind ongoing failures to reach an agreement on cyber security issues between Euro-Atlantic nations on one side and China and Russia on the other. Despite the increased willingness to cooperate, the two models keep clashing in various international forums such as the Budapest Conference on Cyberspace, World Conference on International Telecommunications and others.
I have no intention of getting into a political debate. I am sharing this as an infosec-related cultural curiosity.
To explain the differences, let’s explore Euro-Atlantic definitions first.
Information Security vs IT Security vs Cyber Security – Euro-Atlantic definitions
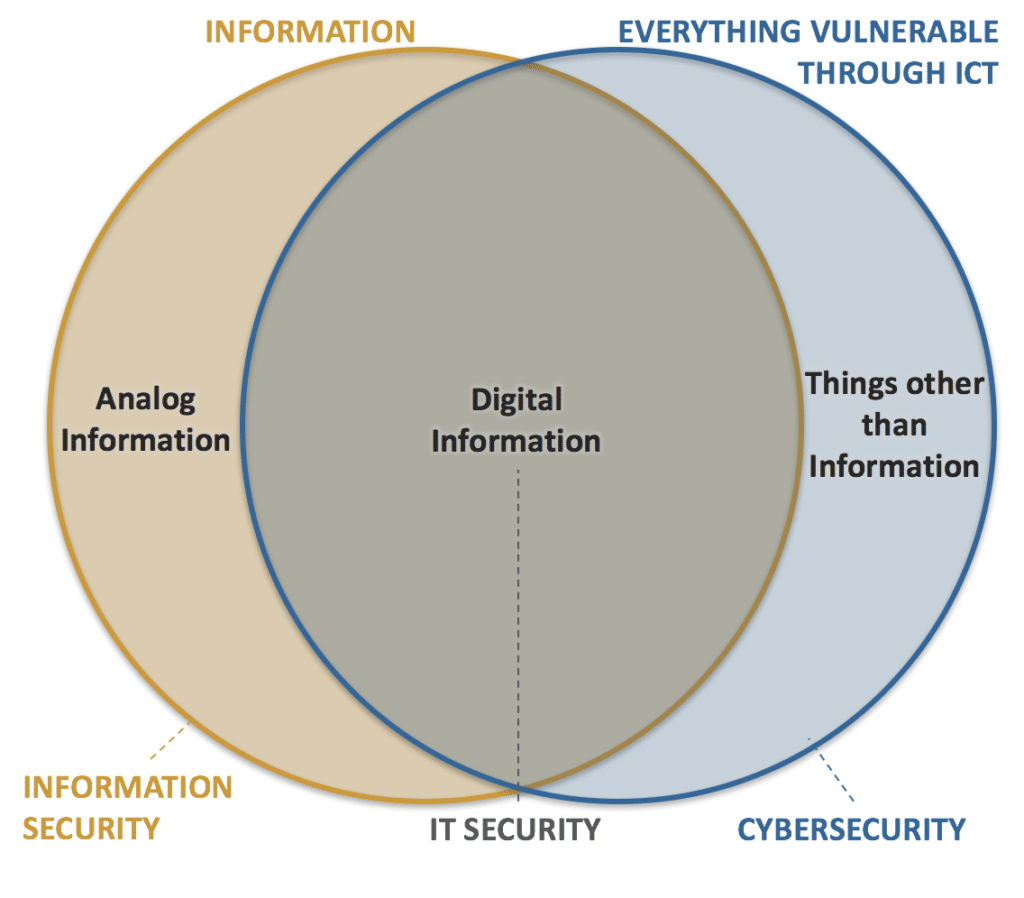
Information security, IT security and cybersecurity are often used interchangeably. Even among the industry professionals. The terms are interrelated and often share the common goals of protecting the confidentiality, integrity and availability of information, however; there are differences between them.
Euro-Atlantic academic and official publications are converging to a common understanding of these concepts.
Information security is fairly broad and goes beyond just the IT aspects. It encompasses classification of information, information security policies and procedures, physical security aspects, legal protections, awareness, and retention of information, regardless of information format. Even when the information is on paper or in heads. Information security is a broader risk management concept.
IT security is an operational objective and it is only concerned with the systems that store, process, transfer and make available electronic data and as such it’s a subset of information security.
Cybersecurity is a bit harder to define because the definitions still have to fully converge. However, in its essence it is about protecting all the things that are vulnerable through information and communications technologies. It includes information but can also include things other than information such as critical infrastructure, connected and self-driving vehicles, connected medical devices, etc.
Simplified Venn diagram of these concepts:
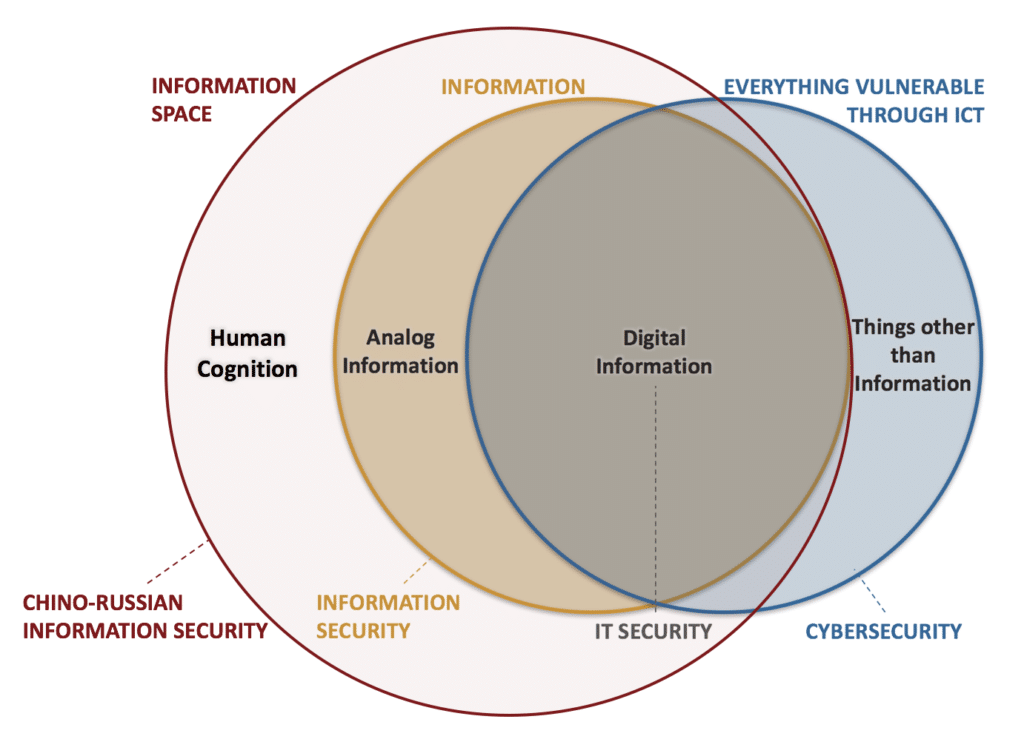
Chino-Russian concept of Information Space
Chino-Russian model differs primarily in its overarching concept of “information space” or “information sphere”, concept that is non-existent or far less defined in Euro-Atlantic.
In Russian Convention on International Information Security [1] “information space” is defined as “the sphere of activity connected with the formation, creation, conversion, transfer, use, and storage of information and which has an effect on individual and social consciousness, the information infrastructure, and information itself.”
Information Security Doctrine of the Russian Federation [3] states “The interests of the individual in the information sphere consist of the exercise of the constitutional rights of man and the citizen to information access, to use of information in the interest of carrying on activities not prohibited by law and of physical, spiritual and intellectual development, as well as of the protection of information that ensures personal security.”
Chinese term 信 息空間 is similarly defined as a domain for communicating with all of the world’s population.
In a simplified summary, Russia and China include human cognition and the effects that human information processing has on individuals and the society as an integral part of their concept of information security.
This extended view of infosec results in interesting situations in which Russian information security practitioners, together with linguists, psychologists and others explore risks and defenses to electronic means of zombification – tools and techniques that act on consciousness and subconsciousness of population to influence irrational behavior. Risks such as psychological warfare, negative influence of sects, mass exposure to psychotropic drugs, zombie-creating (mind control) directed energy weapons, etc. are all being considered in discussions around national protection and in development of national information security doctrine and policies.
This is in contrast to the US, UK, and Euro-Atlantic focus on cyberspace which is defined by US DoD as “Domain characterized by the use of electronics and the electromagnetic spectrum to store, modify, and exchange data via networked systems and associated physical infrastructures.“[4] Euro-Atlantic simply does not consider the mind as an aspect of information space and as a concern for infosec.
In line with the above, Russia and China are concerned about “Information Weapons” as opposed to Euro-Atlantic term of cyber weapons. Information weapons extend the the definition of cyber weapons to “…Information weapons also include means that implement technologies of zombification and psycholinguistic programming.” [2]
Conclusion
Understanding differences in definitions of key infosec concepts between China-Russia and Euro-Atlantic is more than just an academic discussion. These terms underpin national information security policies and the related conceptual gaps are the key challenges to achieving mutual understanding. Euro-Atlantic model prioritizing free exchange of information keeps clashing with the Chino-Russian model advocating stronger national controls of information space. When that happens, it would be prudent to keep in mind that Chino-Russian motives might be significantly more complex than we often assume.
References
- Convention on International Information Security. (2011, September 22). Retrieved October 09, 2016, from http://www.mid.ru/en/foreign_policy/official_documents/-/asset_publisher/CptICkB6BZ29/content/id/191666
- Fedorov, & Tsigichko. (2001). Information Challenges to National and International Security. Moscow: PIR Centre, as quoted in Ventre, D. (2009). Information warfare. London, UK: ISTE.
- Information Security Doctrine of the Russian Federation. (2008, December 29). МИНИСТЕРСТВО ИНОСТРАННЫХ ДЕЛРОССИЙСКОЙ ФЕДЕРАЦИИО. Retrieved October 09, 2016, from http://archive.mid.ru//bdomp/ns-osndoc.nsf/1e5f0de28fe77fdcc32575d900298676/2deaa9ee15ddd24bc32575d9002c442b!OpenDocument
- Joint Terminology for Cyberspace Operations. (2010, November 01). Retrieved October 09, 2016, from http://www.nsci-va.org/CyberReferenceLib/2010-11-joint Terminology for Cyberspace Operations.pdf
For 30+ years, I've been committed to protecting people, businesses, and the environment from the physical harm caused by cyber-kinetic threats, blending cybersecurity strategies and resilience and safety measures. Lately, my worries have grown due to the rapid, complex advancements in Artificial Intelligence (AI). Having observed AI's progression for two decades and penned a book on its future, I see it as a unique and escalating threat, especially when applied to military systems, disinformation, or integrated into critical infrastructure like 5G networks or smart grids. More about me, and about Defence.AI.